Trending
Opinion: How will Project 2025 impact game developers?
The Heritage Foundation's manifesto for the possible next administration could do great harm to many, including large portions of the game development community.

Featured Blog | This community-written post highlights the best of what the game industry has to offer. Read more like it on the Game Developer Blogs or learn how to Submit Your Own Blog Post
A thorough look at the makeup of Stealth Centric Games: examining the relationship between the player avatar and their artificial opponents.

First of all who are these characters and what attributes do they possess that makes them ideal for using stealth? Are they particularly skilled or do they lack the strength and courage to confront threats head-on? These questions are usually answered through the apparent themes the game presents to its players. The thematic presentation of the game generally alludes to the kind of mechanics expected of the game, which of course isn’t exclusive to stealth centric games but most games centered around characters in general.
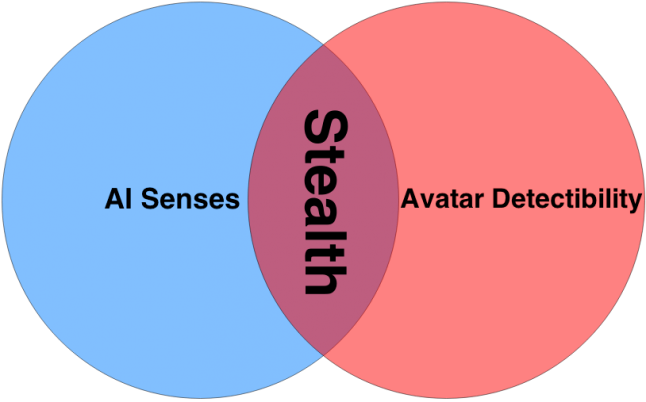
The design of artificial intelligence in stealth centric games is central in creating the desired dynamics for stealth play.We are, however, talking about artificial intelligence for videogames here, as artificial Intelligence (AI) in its traditional sense doesn’t lend itself well to videogames in general. AI in videogames is more used to emulate intelligent behaviors rather than simulate them. What this means is that games require their AI driven opponents to follow limited patterns of behavior. Making these opponents too ‘intelligent’ may even do more harm than good in the game. This refers to videogames that are designed with the intention of adhering to a set of rules that the players understand to be the natural laws of that game world.
The avatars the player inhabits in stealth centric games tend to have very diverse characteristics in general, however some of them are more prevalent than others. These visual and thematic characteristics serve to communicate the available means the player has against the security he’s about to breach.

Breaching through security is a frequent aesthetic of stealth centric games. During his 2006 GDC talk ”Level Building for Stealth Gameplay,” Randy Smith proposed a common aesthetic goal for stealth games as:
[To] create the illusion of a securely guarded area that the player can sneak through by virtue of leveraging their unique abilities and tools to create and exploit security flaws.
The security is typically present in the form of guards, environmental hazards, alarm systems and other measures that are commonly driven by some kind of AI. This article will, mainly look at the guard’s AI relation to the avatar, as guards are the main adversaries the player needs to keep an eye on. For now, we will focus on the player “leveraging their unique abilities and tools to create and exploit security flaws”. These unique abilities usually have the same purpose but manifest themselves differently in different stealth centric games.
Hiding, for example, can be done in different ways, ranging from standing behind vision-obstructing objects to walking among busy crowds and melting into the scenery. In addition to these hiding methods, we have the use of shadows for concealment, which effectively works as a one-way mirror against AI opponents (the player can see them, but they cannot see the player), or using some kind of camouflage to look like the surrounding environment. This can also include using an appropriate disguise to walk among otherwise hostile opponents.

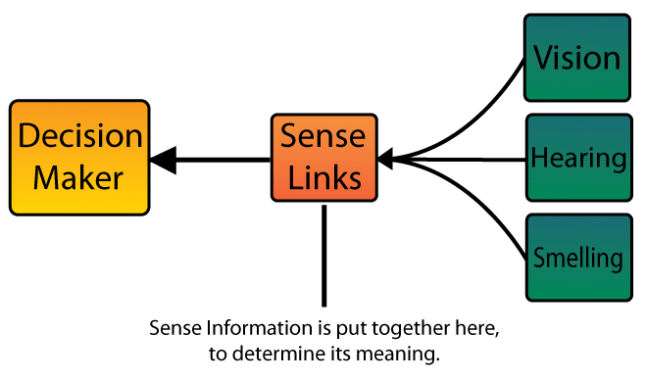
To counter these abilities, the AI-driven opponents need to be able to individually receive and put together information through abstracted ‘senses’, gaining enough knowledge in order to pursue potential intruders. In games that lack a stealth component, the AI opponents tend to be constantly aware of the complete state of the game. So in order to include stealth systems, the game requires AI opponents to have limited knowledge of the avatar's presence.
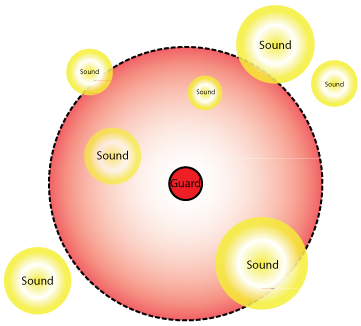
These senses usually come in the form of sight, hearing and sometimes even smelling. These senses serve as a way for the guards to be able to perceive their surroundings, picking up on various clues left by the avatar within the range of their perception. The acquired information is then used by the AI in order to make a decision on how to react to the events taking place.
Contemporary stealth games allow their players to manipulate the way their avatar navigates the environment in order to manage the avatar’s detectability. The pace of movement is altered to reduce sound emissions, which potentially alert threats to the avatar’s location. The guard's hearing sense can pick up on these emissions, through a hearing radius set up around her, from which he can detect sounds emitted by specific entities in the environment. Each sound can be given its own traveling distance and once an emission intersects with the hearing radius it is registered by the guard and the guard reacts accordingly.
The way in which the avatar moves is closely connected to her visibility, as moving naturally changes the environmental conditions that the avatar is present in. For example, this happens when traveling from darker to lighter areas, from empty to crowded streets, etc. So movement affects the avatar’s visibility in general due to the surrounding environment. The guard's sight is usually abstracted by giving it one or multiple calculated angles (view cones) that represent different layers of visual perception. In this case, multiple view cones can be used to represent peripheral and direct vision.
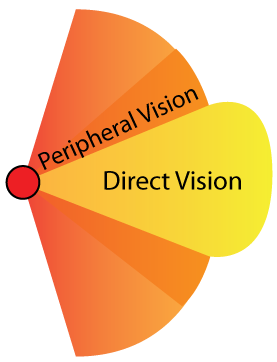
These layers can be set up to react to different aspects of the avatar’s visibility. The guard’s peripheral vision can, for example, be more sensitive to sudden movements. His direct vision detects movement and also determines whether the avatar can be seen in contrast to her environment. As game levels are populated with vision-obstructing objects for the avatar to hide behind, the guard also has to make sure he is actually ‘seeing’ the avatar. To do this a ray (raycast/raytrace) is sent towards the avatar's location and if it hits something before reaching the avatar the guard ignores her presence. Depending on what the game demands, there can be additional visibility checks AI has to perform in order to decide whether or not the guard has detected the avatar.
In some games, adversaries are even able to react to sudden movements when the avatar is present in locations where the guards are otherwise are prevented from directly detecting her due to environmental factors. This emulates the human eye’s sensitivity to movement in general, which adds another abstract layer of detectability management for the player to think about.
For example, if a player is able to hide in the shadows the AI will probably check the degree to which the avatar is concealed by darkness, measuring how likely it is for the guard to detect the avatar from various distances. Camouflage works in a similar way to shadows, with the additional condition that the avatar’s equipped camouflage needs to match her environment. There will probably be instances in which it would be nearly impossible for the guards to detect the avatar when he reaches a certain level of concealment in the case of both camouflage and shadows.
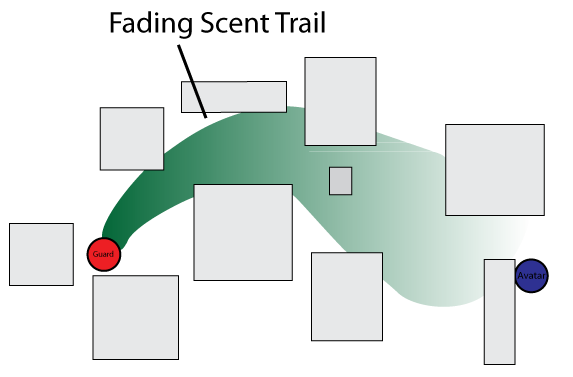
When a guard loses sight of an intruder he is persuing, he will need to start searching in the right direction. This can be addressed by giving the guard a sense of smell. The avatar drops a simulated scent trail as he moves, which the guard can follow once he loses visual contact with the avatar. These scent emissions fade over time as the guard actively searches until the trail runs cold. When this happens the guard loses interest and returns to his former activity.
In order to help manage the threats the avatar encounters, these games commonly include additional physical means, tools or other gadgets that allow the player to tackle or even gauge the dangers ahead. The avatar can typically sneak up on the guards from behind and neutralize them silently. This can also be done from a distance, but some weapons include a penalty of emitting sound, possibly alerting nearby threats.
As mentioned before, the information gathered by the guards’ senses are put together in order for the guard to able to make decisions. These decisions are made whenever they have enough information for a change of to state occur, altering the guards’ behavioral patterns. This kind of operation is a good example of a finite state machine.
These methods can cause guards to be either disposed of indefinitely or knocked out temporarily. This means that they might wake up later by themselves or be awoken by a passing comrade who stumbles upon them. Either way, when a guard is found lying on the ground dead, knocked out or even wakes up by himself, suspicion will arise, possibly initiating a search for threats. To avoid this, the avatar can more often than not, carry the bodies of fallen/unconscious guards, to hide them in locations away from other patrol routes.
Now, there are cases where the player benefits from changing the behavioral state of the guard. Having a guard blocking the avatar’s progression sometimes calls for using distractions to divert attention from the player’s intended path. This can be done by stimulating a guard’s various senses with some type of gadget causing them to enter a curious state, which leads them to investigate the source of the distraction. These tools come in a variety of forms, ranging from noisemaking devices that can be thrown to activate them remotely, to knocking on walls and attracting the adversary to the avatar’s current location.
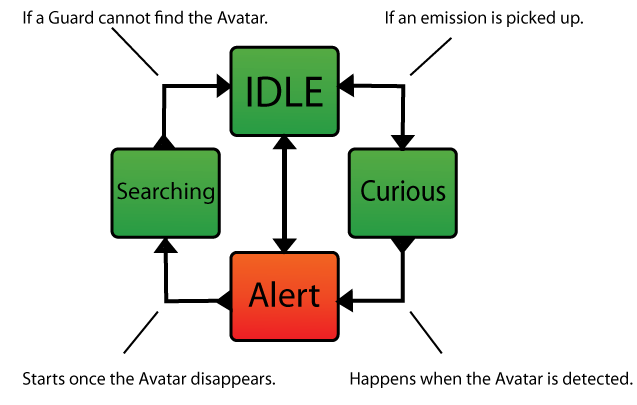
These different states are entered when certain kinds of information are gathered by the guard. The main states are alert and idle patrol, but the game will generally include a variation of states in between. As stated before, these systems also need to serve the game’s design, so complicating them excessively might harm the game.
Guards tend to patrol areas in groups. This means that they are able to share some of the information they’ve acquired with each other when they are near each other. This can be used to make guards work together and that makes them seem more intelligent when they are actively searching for threats while coordinating. Upon detecting the avatar, the guards generally enter an alert state. This is a state in which they are aware of the avatar's location and actively hunting him. In conjunction with this, an alarm system can be set off, leading to the possibility of additional groups of guards rushing towards the avatar.
In the Metal Gear Solid series the game is split into several phases, during which guards have different sets of behaviors they can take on. Each phase is entered through a guard reporting to his high command by radio, eventually changing the state of affairs in the area. When the avatar is detected, the game first goes into an Alert phase in which the number of guards increases. Now that they are aware of the avatar’s location, they actively chase him. If the avatar manages to break visual contact for a while, the game will move into the Evasion phase, in which the guards start searching for the avatar in her last known location. When this phase runs out a Caution phase is entered in which the guards return to their patrol routes with reinforcements still present. Once the Caution phase ends, the reinforcements leave the area, assuming the avatar has left it for another and the Normal phase ensues returning the guards to a state of obliviousness.
In the case of sudden detection, the avatar can in some instances make use of tools that help her escape. These come in the form of gadgets that temporarily stun or blind enemies, giving the avatar enough time to disappear. For example, when the avatar is detected, she can drop a smoke bomb, confusing a group of adversaries. Sometimes the avatar can even halt her pursuers by leaving traps behind, effectively slowing them down or killing them.
Avoiding detection altogether requires the player to do some measure of planning before taking on any challenge. In a game where players spend a substantial amount of time sneaking around, the game must allow for the player to be able to perform some scouting. While the game’s level design must accommodate this, the game should also include some mechanics to aid the player in acquiring further information beyond her field of view. This is practical for increasing the players’ opportunities for improvisation and finding alternate solutions.
Many of these games are designed around their camera model in order to give their players sufficient information about the challenges they are about to encounter. A first-person camera model allows the player to see far away, but gives the player a weak sense of the avatar’s immediate surroundings, while a third-person camera model gives a good view of the avatar’s vicinity but generally doesn’t provide a very good view far ahead. These games sometimes include an ‘over the shoulder’ camera for a better long-distance view, though. For many stealth games taking place in three dimensions, multiple camera models are frequently used to compensate for their different shortcomings. Other means involve context-sensitive camera shifts that happen when the avatar is leaning against the wall near a corner, in order for the avatar to scout around it.
Mark Of The Ninja is a game that intentionally limits the information available to the player. In a game played from a 2D side-scrolling perspective there generally isn’t much stopping the player from seeing what lies behind a large contraption taking up space in the room which is viewed. This game intentionally limits what the player is able to see beyond circle centered on the avatar, which constitutes her field of view. This field of view can be blocked by the level’s surrounding architecture altering its shape, effectively blurring out the content not uncovered by it. The shape of the avatar’s field of view is altered further when she leans towards different directions while climbing or when she is seated on a perch point observing her surroundings. In areas beyond the avatar’s field of view, the player can, however, see expanding visual cues representing different emissions by various entities in the environment, practically marking locations of potential threats and their movements.

There are also mini-map systems in these games that can display the level’s architecture or the guard’s locations and more often than not, both. In different games, these mini-map's systems follow different rules. Some games only mark guards on the mini-map when the player has established visual contact with them, while others don’t require it. Other games make these mini-maps function as sonar detection system similar to that of military radar and so on. Like many other factors, how this feature operates is very dependent on the theme the game wants to project and the kind of stealth play it wants to encourage. However, this feature isn’t always essential and some games exclude these systems entirely.
Other than mini-map systems there are also avatar driven mechanics and gadgets to help the player in further acquiring information beyond her field of view. In Tom Clancy’s Splinter Cell series, these gadgets can come in the form of external cameras that the player can look through, such as snake cameras beneath a door or sticky cameras that can be thrown and stuck onto walls. These are used when a player has little to no access to information about what is ahead.

Mitigating the avatar’s detectability is thus the main player challenge throughout stealth play. So far we’ve covered the avatar assigned abilities to remain undetected whilst navigating hostile environments and the guard’s ability to pick up on the presence of the avatar through emissions they leave behind. The avatar has to breach securely guarded areas in order to reach her goal, so the player needs to manage the degree to which, adversaries are able to pick up on her presence by any means provided.
Unlike other action games, stealth gives the player a narrow failure margin before completely failing at stealth play. Once a player fails at stealth by having their avatar discovered, the game transitions into a different kind of play where the player has to choose between fight or flight. The examination of stealth play doesn’t really end here. There are more topics covered in my thesis, including level design, discussing how to pace stealth levels, balancing multi-path solutions and so on. More research has to be done into what kind stealth play styles there are within the spectrum of stealth centric games. You can also find more information on how I went about my inquiry and the kind sources I used in reaching these conclusions in my thesis, Examining the Essentials of Stealth Game Design.
Read more about:
Featured BlogsYou May Also Like